43 identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.
Word Chapter 3 Flashcards Definition. F3. Term. To advance rightward from one cell to the next in a table, press the ____ key. Definition. TAB. Term. If you want to select the first and third rows in the table in the accompanying figure, you select the first row, and then hold down the ____ key while selecting the third row. Definition. item at position 22 identify and label the following attacks by ... 1) An attacker deceives staff into granting access to sensitive data or protected systems by posing as someone who needs or is authorized to have that access. Whaling 2) A hacker impersonating a reputable company sends emails to high-profile employees requesting them to confirm personal information or send money. Vishing
snap.berkeley.edu Reports True iff the second item (a number) is equal to the number of letters in the first item (a word). false false Insertion sort: Split the input into item 1 (which might not be the smallest) and all the rest of the list. Recursively sort the rest of the list, then insert the one left-over item where it belongs in the list, like adding a ...
Identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.
Spoiler Alert: Does not involve ACTUAL Cosplayers. The title is a means ... /lit/ - Literature - Spoiler Alert: Does not involve ACTUAL Cosplayers. The title is a means of having an all-inclusive mutliverse of characters to choose from. Some of you may remember my VGBabes vs. The Legions of the Undead series. This is the reboot of that. If you'd lik Correct Correct Identify and label the following attacks by dragging ... Correct Correct Identify and label the following attacks by dragging the term on from AA 1 CyberSecurity Chapter 3 Flashcards | Quizlet Which of the following sla statements is true regarding risk analysis? (select two) 1)Annual rate of occurrence (ARO) identifies how often successful threat attacks will occur in a single year 2)Don't implement a countermeasure if the cost is greater than the loss What would choosing to do nothing about an identified risk be acceptable?
Identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used.. Exam SY0-501 topic 1 question 811 discussion - ExamTopics Actual exam question from CompTIA's SY0-501. Question #: 811. Topic #: 1. [All SY0-501 Questions] DRAG DROP -. An attack has occurred against a company. INSTRUCTIONS -. You have been tasked to do the following: Identify the type of attack that is occurring on the network by clicking on the attacker's tablet and reviewing the output. CELLS alive! Since 1994, CELLS alive! has provided students with a learning resource for cell biology, microbiology, immunology, and microscopy through the use of mobile-friendly interactive animations, video, puzzles, quizzes and study aids. 30. Identify and Label the following terms on the | Chegg.com Identify and Label the following terms on the upper air chart below using the initials next to each term: Ridge Axis (R), Trough Axis (T), Warm Air Advection (WA), Cold Air Advection (CA), Divergence (DIV), Convergence (CON) This question hasn't been solved yet Ask an expert Show transcribed image text Expert Answer Transcribed image text: 30. Identify and label the following attacks by dragging the term on the ... An attacker convinces personnel to grant access to sensitive information or protected systemsAn attacker convinces personnel to grant access to sensitive information or protected systemsby pretending to be someone who is authorized and/or requires that access.by pretending to be someone who is authorized and/or requires that access.
Pakistan's human cockroaches | The Express Tribune India could be great help if pakistan change its mind set and get with terms with reality. Help from western countries is the main reason for disparity in pakistan thats why it is a fail state. CS 232 - Test 1 (chapters 1,2,3,4, & 5) - Quizlet (Each attack strategy may be used once, more than once, or not at all.) *Stealing information - Exploitation *Preparing a computer to perform additional tasks in the attack - Staging *Crashing systems - Exploitation *Gathering system hardware information - Reconnaissance *Penetrating system defenses to gain unauthorized access - Breaching Test Out 3 - Subjecto.com Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. Vishing Piggybacking Spam Phishing Whaling Spear phishing Masquerading Spim Tailgating. Match each description to its corresponding term. (Not all options are ... message encapsulation : the process of placing one message format inside another message format (Empty) : the process of determining when to begin sending messages on a network (Empty) : the process of unpacking one message format from another message format More Questions: Modules 5 - 10: Network Fundamentals Group Exam
Foundations Of Centos Linux: Enterprise Linux On The Cheap [PDF ... You can declare your own variable and place data in it. For example, suppose you would like to declare a variable called A, which contains the value test. To do this, all you need to do is to run the command A=test. The equal sign (=) is used to assign the value on its right side to its left side. In other words, A takes the value of test. Instructions:Drag each sentence to the correct category. Not all ... answered • expert verified Instructions:Drag each sentence to the correct category. Not all sentences will be used. Identify the sentences that are written from the first-person and second-person point of view. Letty was not impressed with my brother's car, but at least he had one.You decided you would work with CCNA 200-125 Drag and Drop Questions Full - ITExamAnswers.net Drag the terms on the left onto the appropriate OSI layer on the right. (Not all options are used.) Select and Place: Correct Answer: Answer: Network Layer: + packets + IP address + routing Transport Layer: + udp + segments + windowing 10. DRAG DROP. Refer to the exhibit. You are configuring the router to provide Static NAT for the web server. Identify and label the following attacks by dragging the term on the ... Identify and label the following attacks by dragging the term on the left to the from CMIT- 320 at University of Maryland, University College Study Resources Main Menu
3.5 Flashcards | Quizlet Identify and label the following attacks by dragging the term on the left to the definition on the right. Not all terms are used. 1) An attacker convinces personnel to grant access to sensitive information or protected systems by pretending to be someone who is authorized and/or requires that access. Masquerading
Identify and label the following attacks by dragging the term on the ... Identify and label the following attacks by dragging the term on the left to the Identify and label the following attacks by dragging SchoolNorth Central State College Course TitleCIS MISC Uploaded Bymatthewarnold196 Pages9 This previewshows page 6 - 7out of 9pages. View full document Students who viewed this also studied
CompTIA Security+ Domain 1: Threats, Attacks and Vulnerabilities - Quizlet Asynchronous attack You have installed anti-malware software that checks for viruses in email attachments. You configure the software to quarantine any files with problems. You receive an email with an important attachment, but the attachment is not there. Instead, you see a message that the file has been quarantined by the anti-malware software.
Test Out 1-4 Flashcards | Quizlet You need to dispose of the discs. Which of the following methods should you use to best prevent data extraction from the discs? Write junk data over the discs seven times Degauss the disks Delete the data on the discs Shred the disks Shred the disks Which of the following best describes the concept of due care or due diligence?
Labeling, ranking, sorting, or sentence completion questions Labeling, ranking, sorting, or sentence completion questions Updated 27 Jun 2022 All of these question types require you to position items into an area of the answer box. Answer these kinds of questions on a computer, not on a smartphone. Basic keyboard instructions (applies to most keyboards) Labeling questions Ranking questions Sorting questions
CyberSecurity Chapter 3 Flashcards | Quizlet Which of the following sla statements is true regarding risk analysis? (select two) 1)Annual rate of occurrence (ARO) identifies how often successful threat attacks will occur in a single year 2)Don't implement a countermeasure if the cost is greater than the loss What would choosing to do nothing about an identified risk be acceptable?
Correct Correct Identify and label the following attacks by dragging ... Correct Correct Identify and label the following attacks by dragging the term on from AA 1
Spoiler Alert: Does not involve ACTUAL Cosplayers. The title is a means ... /lit/ - Literature - Spoiler Alert: Does not involve ACTUAL Cosplayers. The title is a means of having an all-inclusive mutliverse of characters to choose from. Some of you may remember my VGBabes vs. The Legions of the Undead series. This is the reboot of that. If you'd lik

























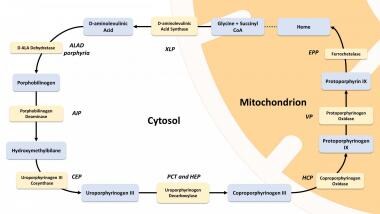


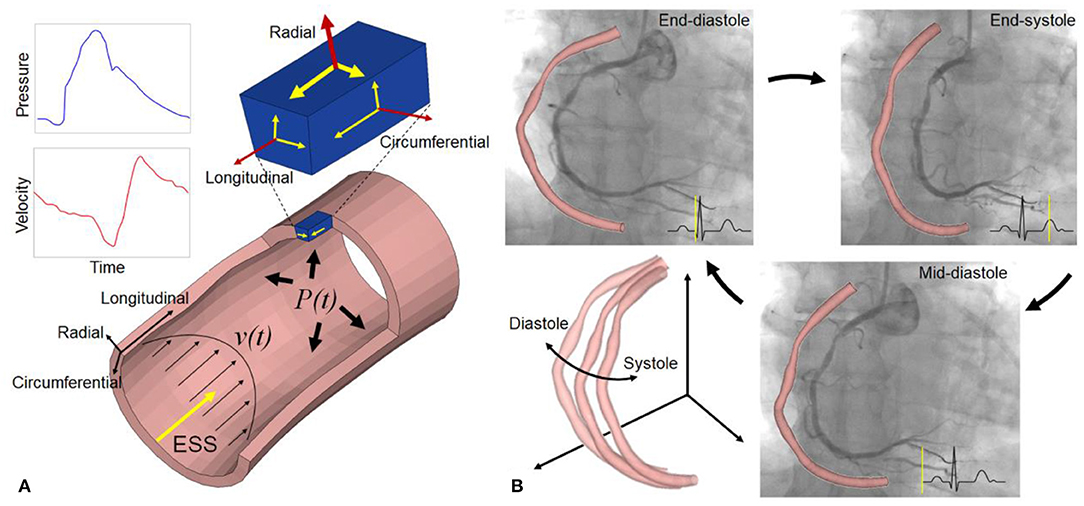






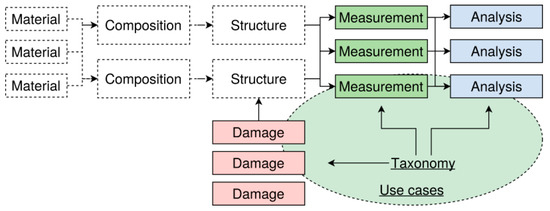
Post a Comment for "43 identify and label the following attacks by dragging the term on the left to the definition on the right. not all terms are used."